The deep web is a concept a good number of persons find difficult to grasp. In the article below, we would be providing you a gentle introduction to the world of the deep web, and you need to know about it.
To many Internet users, anything they cannot find on Google, Yahoo, or Bing does not exist on the Internet. Some even erroneously think that Google is the Internet. In reality, the Internet is much larger than content on Google and other search engines, and to put the record straight, only about 4% of the Internet is accessible via Google and other search engines available on the open Internet.
The vast majority of the Internet is hidden away from crawler-based search engines either purposely or because no website does not have any other website that links to it. The fact remains; the Internet is larger than you think, and that is what this guide on the deep web seeks to discuss.
In this article, you will learn all you need to know about the deep web, including what it is, what makes a website or web pages belong to the deep web, what differentiates it from the dark web, how to access the deep web, and many others.
What is the Deep Web?
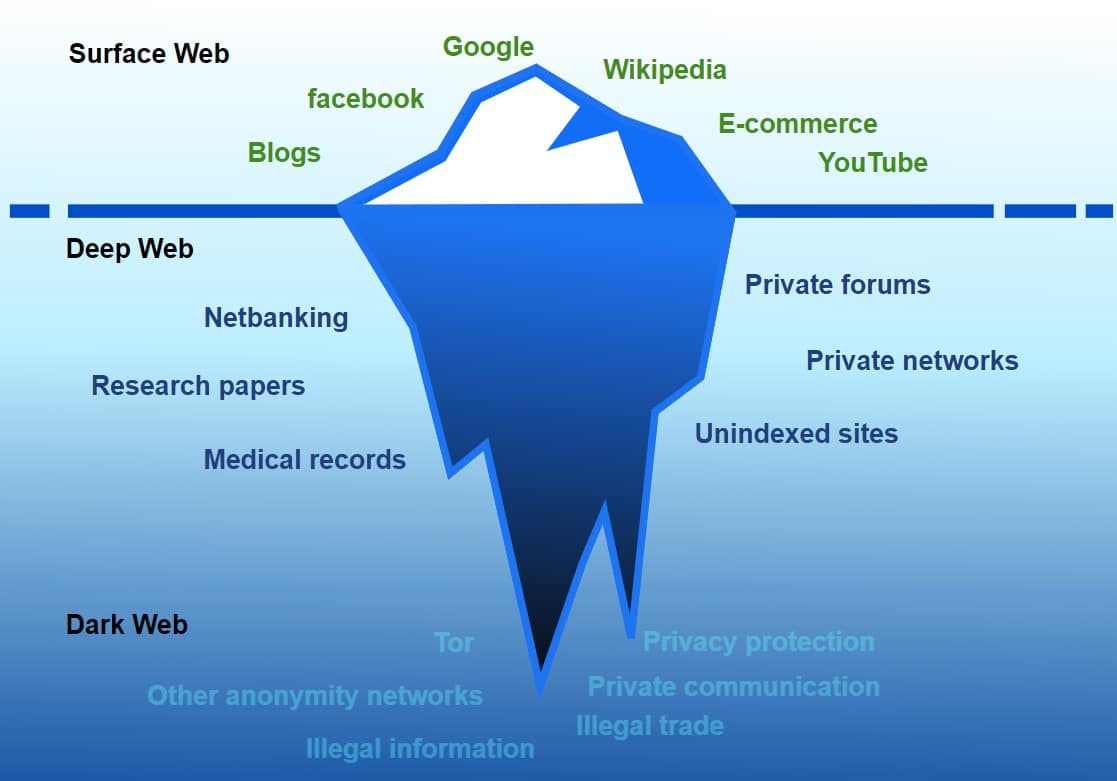
The deep web is that part of the Internet that is inaccessible to search engines. Because it is inaccessible and unidentifiable by search engines, it cannot be crawled, and as such, you cannot access them by merely using a search engine. This means that you cannot get to them accidentally, and visiting deep web content would require you to actually know what you are doing.
Considering the fact that over 90 percent of online experience begins with a search engine, it is wise to say that most people will give up on a search if the content they are looking for is not available on Google or their search engine of choice when in reality, the content is might available somewhere else in the deep web.

It has been stated that the deep web is 90% of the Internet, and you can find all kinds of content you cannot find on the surface web – good, bad, ugly. The Internet-accessible via search engines is known as the surface web and consists of a meager 4%.
Aside from the surface web and the deep web, there is another part of the Internet known as the dark, which comprises 6 percent of the Internet. As you can see, the part of the Internet you cannot access from search engines is about 96%.
Differences Between Deep Web and Dark Web
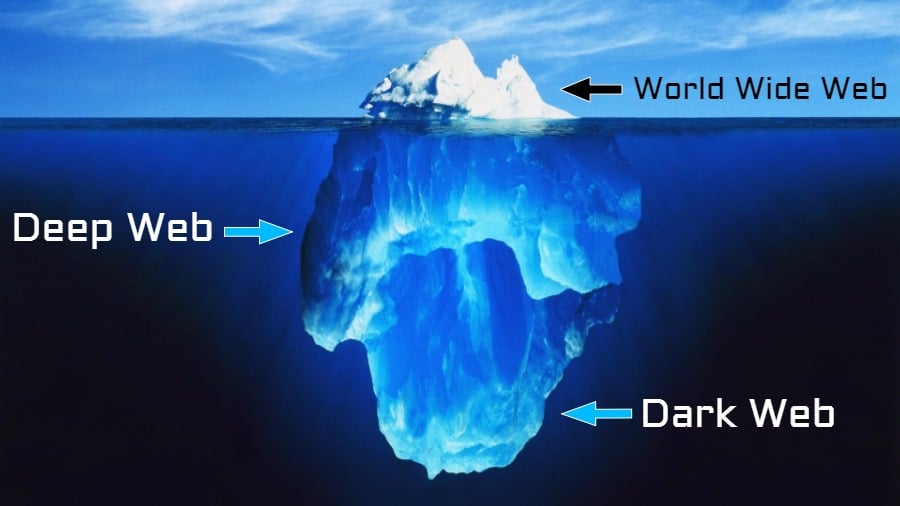
Many people erroneously think that the deep web is synonymous with the dark web. This is not true even though there are similarities between the two. While the deep web can be used for the bad, the good, and the ugly, the dark web is simply meant for only the bad and the unimaginable.
The deep web is the place where you buy hard drugs, hire hitmen, buy weapons, credit card information, and human identities, among other things. If you think of the dark web, then think of that part of the Internet set aside from bad activities and a hub for criminals to carry out their evil intentions.

It might interest you to know that websites on the deep web are developed to be inaccessible by regular users. Most will not have a memorable domain name as they are made of randomly generated letters and digits with the .onion extension.
Except you have been around someone that has visited the dark web, you have probably not heard of a website with a .onion extension. Another thing you need to know about the dark web is that you cannot use your regular web browser to access it. You will need a browser that provides you encryption and makes you anonymous.
Read more, How to Download Torrents Anonymously?
Surface Web and Search Engines

While you might see this heading as unnecessary considering the fact that we are discussing the deep web, understanding how search engines are able to provide their users access to surface web pages is important to understand the deep web and its pages.
The popular search engines are crawler-based search engines. They do not perform any form of magic in other to provide you answers to queries. They make use of computer bots known as web crawlers to index the content of a web page. For any web page to be available on Google, Google must have visited the page and downloaded its content.
Search engine crawlers are fed the first batch of URLs known as seed URLs. From these, the crawler visits each URL and extracts all content, including all the URLs from the page. All of the URLs scrapped are added to the list of URLs to be crawled.

That is how Google discovered content on the Internet. It moves from pages it knows to pages that are linked to that are new to it. Take, for instance, if you host a new page online, you can add it to a page already on Google, and when Google revisits it, it discovers the new page and crawl it too.
How Deep Web Pages are Invisible to Search Engines

The deep web is simply invisible because it is inaccessible to search engines. It might interest you to know that while search engine crawlers such as the Googlebot are highly powerful and could crawl all of the pages in its index within a few days, it is far from perfect.
Search engine crawlers are only able to index web pages with are hyperlinked by other pages. If a page is not linked to from another known page, then there is no way Google or any of its likes will be able to access it.
Some of the web pages are intentionally designed to make them inaccessible to search engines, while some are put into the deep web by mistake. Let take a look at some of the methods used to make websites inaccessible to search engines and put them within the deep web.
- Robots.txt Directives
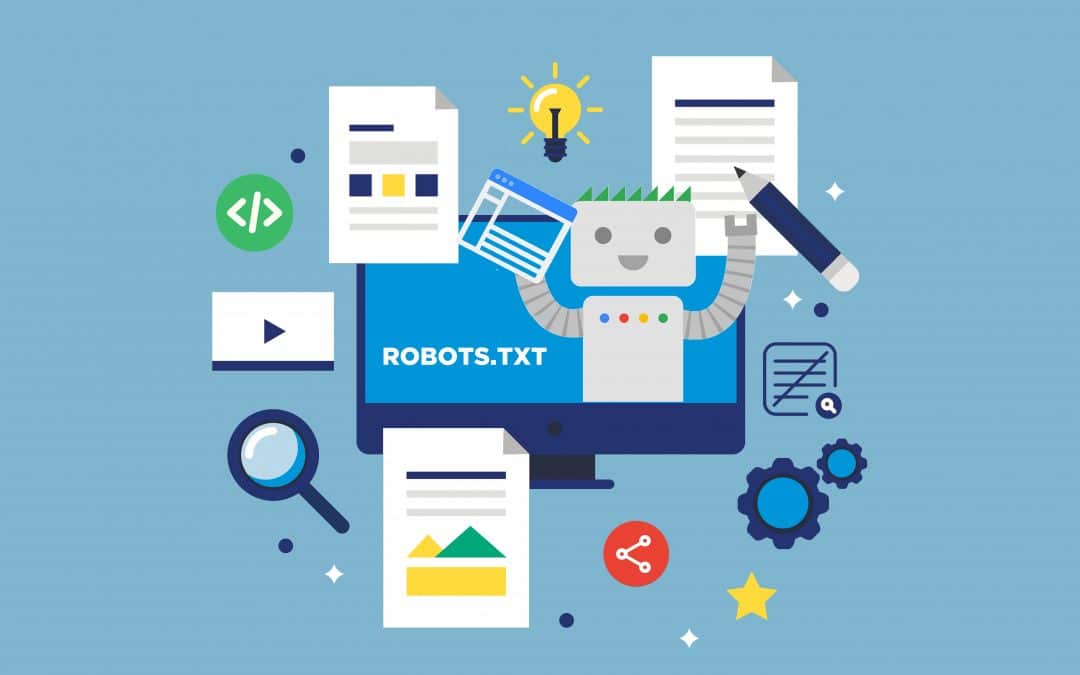
Most website has a robots.txt file that gives directives to web crawlers and bots on how to access it content and web pages it should not access. Most search engines, including Google, Yahoo, and Bing, respect this, and as such, any web page that the directive tells them not to crawl will be left out and not crawled.
- Paywall Blocks
If a web content requires you to make payment in other to access it, then a search engine cannot access it as search engines work freely and would not be ready to access paid content. By putting a paywall for a web page, a crawler is restricted from crawling and thus, prevented from indexing too.
- Content Outside Conventional HTTP Protocols
 Some websites keep some of their websites outside of the conventional http:// and https:// protocols in a bid to keep them away from search engines and away from prying eyes.
Some websites keep some of their websites outside of the conventional http:// and https:// protocols in a bid to keep them away from search engines and away from prying eyes.
- Technically Limited Content
In the past, any content hidden behind JavaScript actions are never indexed by search engines. While Google is able to execute JavaScript, there are still some JavaScript actions that would make websites inaccessible. Also, search engines would not solve Captcha, and any content that is protected by Captcha is skipped by search engine crawlers.
- Database Queries Results
If a page is generated from a database query, then such a page is considered to be a part of the deep web as search engines do not necessarily query databases except a URL string which that is constructed for them.
What is the Deep Web Used for?
When most Internet users hear of the term deep web, they think of it as a beehive of criminal activities. While such can be said to be true for the dark web, such is not entirely true for the deep web. As you have already learned earlier in the article, the deep web is just that part of the Internet that’s not accessible to conventional search engines.
Emails, private social media pages, bank websites, and any other protected web page forms part of the deep web as they are not accessible to the search engines – however, the aforementioned are not bad – the are just private and shouldn’t be made public.
The deep web is used for a range of activities such as the good, the bad, and the ugly. Some of the good uses of the dark web include academic research. There is much academic research, such as scientific papers, that cannot be found on the open web.
You will need to make use of the JSTOR digital library to find these papers. Government and institutional websites can also be part of the deep web. Some Internet users make use of the deep web to bypass paywalls, locational restrictions, and pirated contents without the fear of being caught.
The dark side of the deep web is where things become messy, and that’s why people associated the deep web with the part of the Internet meant for criminally minded individuals. On the deep web, you can purchase credit card details, human IDs, log-in details, fake documents, stolen accounts (Netflix, Spotify, PayPal, etc.), and even bank login details.
It is also the den of drug dealers (marijuana, cocaine) and firearm and other weapons sellers, and illegal good sellers. The truth is that the majority of the deep web is safe, but that part of it that is a den of criminals gives the government a reason to beam its search eyes on the deep web.
How to Access the Deep Web

The whole idea of a web page being accessible to search engines is to make it easy for users to find them. This provides some form of centralization. If a website has been developed to be unfriendly to search engines, then you need to know that they do not want random and unauthorized access.
This also means that there is no centralization, and you will need to know about it as a standalone site and not via a search engine. Below are some of the methods you can use to access web content on the deep web.
- Get A Membership
Some deep web websites have high-quality content, much more than you can find on the open Internet. In fact, it might interest you to know that the amount of valuable content in the deep web is much more than the surface web and, as such, the reason for being hidden in other to keep the content in a close circle.
Take, for instance, peer-reviewed journals, researches, and records that are not made available to the general public. Some of these websites would require you to join a professional association, make payment, or carry out certain tasks in other to be granted access.
- Get an Insider to Grant you Access
For some of the websites, there is no way you can have access without an existing user referring you. Sites like this are even hidden from the public, and there is no way you will know about them except a member let you know. You need to be in the right circle and network to be able to access sites like these.
- Use an Organization Network as a Proxy
For some web content on the deep web, only requests from certain IP addresses are allowed access. Take, for instance; there are some academic websites that would only grant you access if you are using computers in your school library. If you suspect your school or organization’s IP address is whitelisted, you could connect to their network and use them to gain access.
- Use Specialized Deep Web Search Engines
There are some search engines that will provide you access to content not available on the surface web. But these are not your conventional search engines and, in some cases, can even be seen as invisible web directories. Some of the best-known examples include Librarian’s Internet Index, Google Book Search, and JSTOR.
Browsers and Tools for Accessing the Deep Web
There is a misconception about the browser you should use when surfing the deep web. Many would tell you that your conventional browser would not be able to access deep web websites. If you hear this, then just know that the person telling you this is mistaking the deep web for the dark web.
You cannot use your conventional browser such as Chrome to access websites on the dark web – you will need a darknet browser like the popular Tor browser downloadable here. This browser routes your traffic via many relay nodes and dissociates your IP address from your traffic, thereby keeping you anonymous.
However, if all you want is to access a regular website (non-onion website) on the deep web, then there is no need to use the Tor browser. You can use your regular web browser but make sure you have a proxy server or VPN configured in other to hide your real IP address.
- For the proxy server, you can get high-quality proxies from Bright Data, Smartproxy, and MyPrivateProxy.
- For the VPN service, I would suggest you use ExpressVPN, NordVPN, and Torguard VPN.
The deep web does not conform to many of the privacy policies, and you wouldn’t want someone with a bad intent to trail and track you.
Related, Track someone's IP from Instagram, Snapchat, and Facebook Messenger
The advantage of using your regular browser and proxy over the Tor browser is that the Tor browser is very slow, and your ISP can easily tell you are using the Tor network.
Payment on the Deep Web
Unlike on the open web that you mostly get content for free, on the deep web, there is usually no free meal, and you will have to make a payment, or the site looks for a way to monetize you. I am not saying they are no free sites as one can argue that pirated content is freely available on the deep web.
However, a good number of services or content will require you to make payment. While some sites would accept methods via regular channels such as PayPal and credit cards, a bulk of deep web merchants only accept cryptocurrencies as payment.

Aside from Bitcoin, which is the most popular cryptocurrency, other currencies accepted on the deep web include Litecoin and Monero. The acceptance of crypto in the deep and dark web is one of the reasons governments of nations are planning to ban or regulate cryptocurrency.
Interestingly, the major reason why cryptocurrency appeals to deep web merchants and visitors is because of its anonymous and privacy-supporting nature.
Risks Associated with the Deep Web

In this section of the article, you will be learning about some of the problems associated with the deep web.
- Scams
One thing you need to know is that while you can be scammed easily on surface Internet, the chances are more in the deep web, and there is nothing you can do about it when such occur. You could be asked to pay for a book using Bitcoin, and after making payment, the seller will vanish.
- Identity Theft
 While using the deep web, your identity and information such as name, email address, and contact address can be stolen and sold to other users. It is important you generate fake identities to use while accessing sites on the deep web.
While using the deep web, your identity and information such as name, email address, and contact address can be stolen and sold to other users. It is important you generate fake identities to use while accessing sites on the deep web.
- Malware and Virus

If you are not careful and do not have anti-virus and anti-malware software on your computer, I will advise against accessing the deep web as you might be a victim of malicious software such as keylogger, ransomware, botnet software, and phishing software.
- Government Monitoring
 While using a proxy server, you could become a subject of monitoring if you are found visiting certain websites on the deep web. Some of the sites are even illegal to visit, and trying to even use a proxy server to bypass monitoring in itself can also be an offense in countries like China.
While using a proxy server, you could become a subject of monitoring if you are found visiting certain websites on the deep web. Some of the sites are even illegal to visit, and trying to even use a proxy server to bypass monitoring in itself can also be an offense in countries like China.
Is the Deep Web Illegal?
Accessing the deep web is not illegal. Think about it; your bank website, social media accounts, emails, and the many password-protected platforms you access are all part of the deep web – and are all completely legal. The major issue is actually what your intentions are and what you want to achieve that makes it illegal.
While a journalist carrying out research and buying leaked documents might not be illegal, you buying marijuana is completely illegal. Think about it – if what you intend to do is illegal, then using the deep web for it is also illegal.
Related,
From the article, you can tell that the Internet is wider than what is available on Google as over 96 percent of the content of the Internet is not accessible to Google and other conventional search engines.
That content you are looking for is probably somewhere hidden deep inside of the Internet – you will need to look deeper into the deep web, but as you do so, you will need to stay protected and aware of the risks associated with visiting the deep web.
